Sunburst Solarwinds Backdoor
Technical analysis of SUNBURST SolarWinds Backdoor
 |
| Sunburst Solarwinds Backdoor |
Identification
|
Vendor |
Detection |
|
TrendMicro |
Backdoor.MSIL.SUNBURST.A |
|
Microsoft |
Trojan:MSIL/Solorigate.BR!dha |
|
Kaspersky |
HEUR:Backdoor.MSIL.SunBurst.gen |
The
following table contains a list of artifacts that had been analyzed within this
document.
|
PE
timestamp |
MD5 |
Size in
bytes |
File name |
Description |
|
2020/05/11
Mon 21:32:40 UTC |
846E27A652A5E1BFBD0DDD38A16DC865 |
1003.98 KB
(1028072 bytes) |
SolarWinds.Orion.Core.BusinessLayer-SUNBURST.dll |
Main
payload |
Interesting
The most interesting for me is signature of file, file is signed but it contains a backdoor as shown in figure below.
 |
| Sunburst Solarwinds |
Summary
Sunburst has been widespread across organizations in a supply-chain attack. Backdoor. Sunburst uses multiple obfuscated blacklists to identify security and antivirus tools running as processes, services, and drivers. It stores this information for later stages of an attack.
Technical details
It gets the current process name then gets the hash of the process then convert name of process to lowercase and compare hash with value called 17291806236368054941UL as shown in figure below.
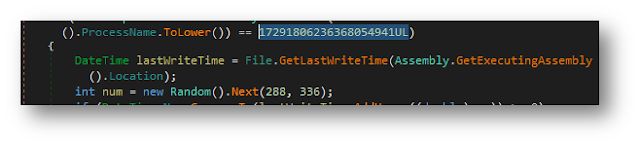 |
| Sunburst Solarwinds |
It gets a hash of a lower process using an algorithm called FNV-1a 64 bit as shown in figure below and do XOR result with value called 6605813339339102567UL.
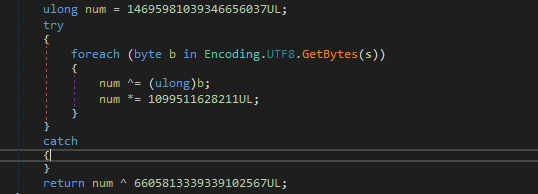 |
| Sunburst Solarwinds |
So if you reverse the algorithm you will figure out that the value 17291806236368054941UL will represent the process name called solarwinds.businesslayerhost.
It gets a random number from 288 to 336, that means malware will run from 12 to 14 days once it finds the process name called solarwinds.businesslayerhost as shown in figure below.
 |
| Sunburst Solarwinds |
The malware is really obfuscated, so I tried to DE obfuscate as much as possible.
Configuration of network
It gets network
configuration as shown in figure below when executed some command like.
 |
| Sunburst Solarwinds |
Commands
- Select * From Win32_NetworkAdapterConfiguration where IPEnabled=true.
- Description.
- MACAddress.
- DHCPEnabled.
- DHCPServer.
- DNSHostName.
- DNSDomainSuffixSearchOrder.
- DNSServerSearchOrder.
- IPAddress.
- IPSubnet.
- DefaultIPGateway.
- Select * From Win32_OperatingSystem.
- Caption.
- OSArchitecture.
- InstallDate.
- Organization.
- RegisteredUser.
- Version.
If it can’t get the operating system version it will cause an exception called “[E] {0} {1} {2}” as shown in figure below.
 |
| Sunburst Solarwinds |
It gets user id when it access registry path called HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography specially value called MachineGuid then gets MD5 of machine GUID as shown in figure below.
 |
| Sunburst Solarwinds |
 |
| Sunburst Solarwinds |
It gets a hash of current processes using an algorithm called FNV-1a 64 bit as shown in figure below, if it finds one of these processes already running, then malware exits.
 |
| Sunburst Solarwinds |
|
Hash |
Process name |
|
2597124982561782591UL |
apimonitor-x64 |
|
2600364143812063535UL |
apimonitor-x86 |
|
13464308873961738403UL |
autopsy64 |
|
4821863173800309721UL |
autopsy |
|
12969190449276002545UL |
autoruns64 |
|
3320026265773918739UL |
autoruns |
|
12094027092655598256UL |
autorunsc64 |
|
10657751674541025650UL |
autorunsc |
|
11913842725949116895UL |
binaryninja |
|
5449730069165757263UL |
blacklight |
|
292198192373389586UL |
cff explorer |
|
12790084614253405985UL |
cutter |
|
5219431737322569038UL |
de4dot |
|
15535773470978271326UL |
debugview |
|
7810436520414958497UL |
diskmon |
|
13316211011159594063UL |
dnsd |
|
13825071784440082496UL |
dnspy |
|
14480775929210717493UL |
dotpeek32 |
|
14482658293117931546UL |
dotpeek64 |
|
8473756179280619170UL |
dumpcap |
|
3778500091710709090UL |
evidence center |
|
8799118153397725683UL |
exeinfope |
|
12027963942392743532UL |
fakedns |
|
576626207276463000UL |
fakenet |
|
7412338704062093516UL |
ffdec |
|
682250828679635420UL |
fiddler |
|
13014156621614176974UL |
fileinsight |
|
18150909006539876521UL |
floss |
|
10336842116636872171UL |
gdb |
|
12785322942775634499UL |
hiew32demo |
|
13260224381505715848UL |
hiew32 |
|
17956969551821596225UL |
hollows_hunter |
|
8709004393777297355UL |
idaq64 |
|
14256853800858727521UL |
idaq |
|
8129411991672431889UL |
idr |
|
15997665423159927228UL |
ildasm |
|
10829648878147112121UL |
ilspy |
|
9149947745824492274UL |
jd-gui |
|
3656637464651387014UL |
lordpe |
|
3575761800716667678UL |
officemalscanner |
|
4501656691368064027UL |
ollydbg |
|
10296494671777307979UL |
pdfstreamdumper |
|
14630721578341374856UL |
pe-bear |
|
4088976323439621041UL |
pebrowse64 |
|
9531326785919727076UL |
peid |
|
6461429591783621719UL |
pe-sieve32 |
|
6508141243778577344UL |
pe-sieve64 |
|
10235971842993272939UL |
pestudio |
|
2478231962306073784UL |
peview |
|
9903758755917170407UL |
pexplorer |
|
14710585101020280896UL |
ppee |
|
13611814135072561278UL |
procdump64 |
|
2810460305047003196UL |
procdump |
|
2032008861530788751UL |
processhacker |
|
27407921587843457UL |
procexp64 |
|
6491986958834001955UL |
procexp |
|
2128122064571842954UL |
procmon |
|
10484659978517092504UL |
prodiscoverbasic |
|
8478833628889826985UL |
py2exedecompiler |
|
10463926208560207521UL |
r2agent |
|
7080175711202577138UL |
rabin2 |
|
8697424601205169055UL |
radare2 |
|
7775177810774851294UL |
ramcapture64 |
|
16130138450758310172UL |
ramcapture |
|
506634811745884560UL |
reflector |
|
18294908219222222902UL |
regmon |
|
3588624367609827560UL |
resourcehacker |
|
9555688264681862794UL |
retdec-ar-extractor |
|
5415426428750045503UL |
retdec-bin2llvmir |
|
3642525650883269872UL |
retdec-bin2pat |
|
13135068273077306806UL |
retdec-config |
|
3769837838875367802UL |
retdec-fileinfo |
|
191060519014405309UL |
retdec-getsig |
|
1682585410644922036UL |
retdec-idr2pat |
|
7878537243757499832UL |
retdec-llvmir2hll |
|
13799353263187722717UL |
retdec-macho-extractor |
|
1367627386496056834UL |
retdec-pat2yara |
|
12574535824074203265UL |
retdec-stacofin |
|
16990567851129491937UL |
retdec-unpacker |
|
8994091295115840290UL |
retdec-yarac |
|
13876356431472225791UL |
rundotnetdll |
|
14968320160131875803UL |
sbiesvc |
|
14868920869169964081UL |
scdbg |
|
106672141413120087UL |
scylla_x64 |
|
79089792725215063UL |
scylla_x86 |
|
5614586596107908838UL |
shellcode_launcher |
|
3869935012404164040UL |
solarwindsdiagnostics |
|
3538022140597504361UL |
sysmon64 |
|
14111374107076822891UL |
sysmon |
|
7982848972385914508UL |
task explorer |
|
8760312338504300643UL |
task explorer-x64 |
|
17351543633914244545UL |
tcpdump |
|
7516148236133302073UL |
tcpvcon |
|
15114163911481793350UL |
tcpview |
|
15457732070353984570UL |
vboxservice |
|
16292685861617888592UL |
win32_remote |
|
10374841591685794123UL |
win64_remotex64 |
|
3045986759481489935UL |
windbg |
|
17109238199226571972UL |
windump |
|
6827032273910657891UL |
winhex64 |
|
5945487981219695001UL |
winhex |
|
|
|
|
8052533790968282297UL |
winobj |
|
17574002783607647274UL |
wireshark |
|
3341747963119755850UL |
x32dbg |
|
14193859431895170587UL |
x64dbg |
|
17439059603042731363UL |
xwforensics64 |
|
17683972236092287897UL |
xwforensics |
|
700598796416086955UL |
redcloak |
|
3660705254426876796UL |
avgsvc |
|
12709986806548166638UL |
avgui |
|
3890794756780010537UL |
avgsvca |
|
2797129108883749491UL |
avgidsagent |
|
3890769468012566366UL |
avgsvcx |
|
14095938998438966337UL |
avgwdsvcx |
|
11109294216876344399UL |
avgadminclientservice |
|
1368907909245890092UL |
afwserv |
|
11818825521849580123UL |
avastui |
|
8146185202538899243UL |
avastsvc |
|
2934149816356927366UL |
aswidsagent |
|
13029357933491444455UL |
aswidsagenta |
|
6195833633417633900UL |
aswengsrv |
|
2760663353550280147UL |
avastavwrapper |
|
16423314183614230717UL |
bccavsvc |
|
2532538262737333146UL |
psanhost |
|
4454255944391929578UL |
psuaservice |
|
6088115528707848728UL |
psuamain |
|
13611051401579634621UL |
avp |
|
18147627057830191163UL |
avpui |
|
17633734304611248415UL |
ksde |
|
13581776705111912829UL |
ksdeui |
|
7175363135479931834UL |
tanium |
|
3178468437029279937UL |
taniumclient |
|
13599785766252827703UL |
taniumdetectengine |
|
6180361713414290679UL |
taniumendpointindex |
|
8612208440357175863UL |
taniumtracecli |
|
8408095252303317471UL |
taniumtracewebsocketclient64 |
Attacker repeated checking for a process called ppee 2 times.
Configurations search
It gets Path Name of system driver using sql command Select * From Win32_SystemDriver. It searches for specific services as shown in figure below.
|
Hash |
Services name |
|
17097380490166623672UL |
cybkerneltracker.sys |
|
15194901817027173566UL |
atrsdfw.sys |
|
12718416789200275332UL |
eaw.sys |
|
18392881921099771407UL |
rvsavd.sys |
|
3626142665768487764UL |
dgdmk.sys |
|
12343334044036541897UL |
sentinelmonitor.sys |
|
397780960855462669UL |
hexisfsmonitor.sys |
|
6943102301517884811UL |
groundling32.sys |
|
13544031715334011032UL |
groundling64.sys |
|
11801746708619571308UL |
safe-agent.sys |
|
18159703063075866524UL |
crexecprev.sys |
|
835151375515278827UL |
psepfilter.sys |
|
16570804352575357627UL |
cve.sys |
|
1614465773938842903UL |
brfilter.sys |
|
12679195163651834776UL |
brcow_x_x_x_x.sys |
|
2717025511528702475UL |
lragentmf.sys |
|
17984632978012874803UL |
libwamf.sys |
Configuration of services
It access registry path SYSTEM\CurrentControlSet\services then gets a value name called start and searches for configuration of services as shown in figure below.
|
Hash |
Service name |
|
5183687599225757871UL |
msmpeng |
|
917638920165491138UL |
windefend |
|
10063651499895178962UL |
mssense |
|
16335643316870329598UL |
sense |
|
10501212300031893463UL |
microsoft.tri.sensor |
|
155978580751494388UL |
microsoft.tri.sensor.updater |
|
17204844226884380288UL |
cavp |
|
5984963105389676759UL |
cb |
|
11385275378891906608UL |
carbonblack |
|
13693525876560827283UL |
carbonblackk |
|
17849680105131524334UL |
cbcomms |
|
18246404330670877335UL |
cbstream |
|
8698326794961817906UL |
csfalconservice |
|
9061219083560670602UL |
csfalconcontainer |
|
11771945869106552231UL |
csagent |
|
9234894663364701749UL |
csdevicecontrol |
|
8698326794961817906UL |
csfalconservice |
|
15695338751700748390UL |
xagt |
|
640589622539783622UL |
xagtnotif |
|
15695338751700748390UL |
xagt |
|
9384605490088500348UL |
fe_avk |
|
6274014997237900919UL |
fekern |
|
15092207615430402812UL |
feelam |
|
3320767229281015341UL |
fewscservice |
|
3200333496547938354UL |
ekrn |
|
14513577387099045298UL |
eguiproxy |
|
607197993339007484UL |
egui |
|
15587050164583443069UL |
eamonm |
|
9559632696372799208UL |
eelam |
|
4931721628717906635UL |
ehdrv |
|
3200333496547938354UL |
ekrn |
|
2589926981877829912UL |
ekrnepfw |
|
17997967489723066537UL |
epfwwfp |
|
14079676299181301772UL |
ekbdflt |
|
17939405613729073960UL |
epfw |
|
521157249538507889UL |
fsgk32st |
|
14971809093655817917UL |
fswebuid |
|
10545868833523019926UL |
fsgk32 |
|
15039834196857999838UL |
fsma32 |
|
14055243717250701608UL |
fssm32 |
|
5587557070429522647UL |
fnrb32 |
|
12445177985737237804UL |
fsaua |
|
17978774977754553159UL |
fsorsp |
|
17017923349298346219UL |
fsav32 |
|
17624147599670377042UL |
f-secure gatekeeper handler starter |
|
16066651430762394116UL |
f-secure network request broker |
|
13655261125244647696UL |
f-secure webui daemon |
|
12445177985737237804UL |
fsaua |
|
3421213182954201407UL |
fsma |
|
14243671177281069512UL |
fsorspclient |
|
16112751343173365533UL |
f-secure gatekeeper |
|
3425260965299690882UL |
f-secure hips |
|
9333057603143916814UL |
fsbts |
|
3413886037471417852UL |
fsni |
|
7315838824213522000UL |
fsvista |
|
13783346438774742614UL |
f-secure filter |
|
2380224015317016190UL |
f-secure recognizer |
|
3413052607651207697UL |
fses |
|
3407972863931386250UL |
fsfw |
|
10393903804869831898UL |
fsdfw |
|
12445232961318634374UL |
fsaus |
|
3421197789791424393UL |
fsms |
|
541172992193764396UL |
fsdevcon |
interesting subnets
It makes depolymerization of IP addresses so malware receives a DNS A record response pointing to one of these subnets as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded ip |
Decoded ip |
|
MzTQA0MA |
10.0.0.0 |
|
MzI11TMAQQA |
255.0.0.0 |
|
MzQ30jM00zPQMwAA |
172.16.0.0 |
|
MzI11TMyMdADQgA |
255.240.0.0 |
|
M7Q00jM0s9Az0DMAAA |
192.168.0.0 |
|
MzI11TMCYgM9AwA |
255.255.0.0 |
|
MzIy0TMAQQA |
224.0.0.0 |
|
MzIx0ANDAA |
240.0.0.0 |
|
S0s2MLCyAgA |
fc00:: |
|
S0s1MLCyAgA |
fc00:: |
|
S0tNNrCyAgA |
fec0:: |
|
S0szMLCyAgA |
ff00:: |
|
S0szMLCyAgA |
ff00:: |
|
MzHUszDRMzS11DMAAA |
41.84.159.0 |
|
MzI11TOCYgMA |
255.255.255.0 |
|
MzfRMzQ00TMy0TMAAA |
74.114.24.0 |
|
MzI11TMCYRMLPQMA |
255.255.248.0 |
|
MzQ10TM0tNAzNDHQMwAA |
154.118.140.0 |
|
MzI11TOCYgMA |
255.255.255.0 |
|
MzI01zM0M9Yz1zMAAA |
217.163.7.0 |
|
MzI11TOCYgMA |
255.255.255.0 |
|
MzLQMzQx0ANCAA |
20.140.0.0 |
|
MzI11TMyNdEz0DMAAA |
255.254.0.0 |
|
szTTMzbUMzQ30jMAAA |
96.31.172.0 |
|
MzI11TOCYgMA |
255.255.255.0 |
|
MzQ21DMystAzNNIzAAA |
131.228.12.0 |
|
MzI11TMCYyM9AwA |
255.255.252.0 |
|
MzQx0bMw0zMyMtMzAAA |
144.86.226.0 |
|
MzI11TOCYgMA |
255.255.255.0 |
|
s9AztNAzNDHRMwAA |
8.18.144.0 |
|
MzI11TMCYxM9AwA |
255.255.254.0 |
|
M7TQMzQ20ANCAA |
18.130.0.0 |
|
MzI11TMCYgM9AwA |
255.255.0.0 |
|
MzfUMzQ10jM11jMAAA |
71.152.53.0 |
|
MzI11TOCYgMA |
255.255.255.0 |
|
s7TUM7fUM9AzAAA |
99.79.0.0 |
|
MzI11TMCYgM9AwA |
255.255.0.0 |
|
szDXMzK20LMw0DMAAA |
87.238.80.0 |
|
MzI11TMCYRMLPQMA |
255.255.248.0 |
|
M7S01DMyMNQzNDTXMwAA |
199.201.117.0 |
|
MzI11TOCYgMA |
255.255.255.0 |
|
M7Qw0TM30jPQMwAA |
184.72.0.0 |
|
MzI11TMyNdEz0DMAAA |
255.254.0.0 |
Pattern search
It checks for these domains in active directory as shown in figure and table below.
 |
| Sunburst Solarwinds |
|
Pattern Hash |
Decoded Of Pattern |
|
1109067043404435916UL |
swdev.local |
|
15267980678929160412UL |
swdev.dmz |
|
8381292265993977266UL |
lab.local |
|
3796405623695665524UL |
lab.na |
|
8727477769544302060UL |
emea.sales |
|
10734127004244879770UL |
cork.lab |
|
11073283311104541690UL |
dev.local |
|
4030236413975199654UL |
dmz.local |
|
7701683279824397773UL |
pci.local |
|
5132256620104998637UL |
saas.swi |
|
5942282052525294911UL |
lab.rio |
|
4578480846255629462UL |
lab.brno |
|
16858955978146406642UL |
apac.lab |
It assigns pattern list, which seems to be regular expression as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded Regex |
Decoded Of Regex |
|
07DP1NSIjkvUrYqtidPUKEktLoHzVTQB |
(?i)([^a-z]|^)(test)([^a-z]|$) |
|
07DP1NQozs9JLCrPzEsp1gQA |
(?i)(solarwinds) |
Configuration manger
It reads configurations manger then applied 3 switch cases
- Truncate
- New
- Append
As shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded Report Status |
Decoded Report Status |
|
C0otyC8qCU8sSc5ILQpKLSmqBAA |
ReportWatcherRetry |
It reads services status as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded Service Status |
Decoded Service Status |
|
C0otyC8qCU8sSc5ILQrILy4pyM9LBQA |
ReportWatcherPostpone |
Check for server connection
It checks for connection of Solarwinds server as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded Host |
Decoded Host |
|
SyzI1CvOz0ksKs/MSynWS87PBQA |
api.solarwinds.com |
Domain Generation Algorithm(DGA)
It gets the status of these domains as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded Domain |
Decoded Domain |
|
SywrLstNzskvTdFLzs8FAA |
avsvmcloud.com |
|
SywoKK7MS9ZNLMgEAA |
appsync-api |
|
Sy3VLU8tLtE1BAA |
eu-west-1 |
|
Ky3WLU8tLtE1AgA |
us-west-2 |
|
Ky3WTU0sLtE1BAA |
us-east-1 |
|
Ky3WTU0sLtE1AgA |
us-east-2 |
So Final DGA will be one of these.
- appsync-api.eu-west-1[.]avsvmcloud[.]com.
- appsync-api.us-west-2[.]avsvmcloud[.]com.
- appsync-api.us-east-1[.]avsvmcloud[.]com.
- appsync-api.us-east-2[.]avsvmcloud[.]com.
It initializes new pipe id as shown in figure below.
|
Encoded Pipe ID |
M7UwTkm0NDHVNTNKTNM1NEi10DWxNDDSTbRIMzIwTTY3SjJKBQA |
|
Decoded Pipe ID |
583da945-62af-10e8-4902-a8f205c72b2e |
Information gathering
It gets information from registry like all users, current configuration, local machine etc as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded Registry path |
Decoded Registry path |
|
8/B2jYx39nEMDnYNjg/y9w8BAA |
HKEY_CLASSES_ROOT |
|
8/B2DgIA |
HKCR |
|
8/B2jYx3Dg0KcvULiQ8Ndg0CAA |
HKEY_CURRENT_USER |
|
8/B2DgUA |
HKCU |
|
8/B2jYz38Xd29In3dXT28PRzBQA |
HKEY_LOCAL_MACHINE |
|
8/D28QUA |
HKLM |
|
8/B2jYwPDXYNCgYA |
HKEY_USERS |
|
8/AOBQA |
HKU |
|
8/B2jYx3Dg0KcvULiXf293PzdAcA |
HKEY_CURRENT_CONFIG |
|
8/B2dgYA |
HKCC |
|
8/B2jYwPcA1y8/d19HN2jXdxDHEEAA |
HKEY_PERFOMANCE_DATA |
|
8/AOcAEA |
HKPD |
|
8/B2jYx3ifSLd3EMcQQA |
HKEY_DYN_DATA |
|
8/B2cQEA |
HKDD |
Get Sid of current account
It gets the security identifier of the current user as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded value |
Decoded value |
|
C9Y11DXVBQA |
S-1-5- |
|
0zU1MAAA |
-500 |
|
c0zJzczLLC4pSizJLwIA |
Administrator |
|
C07NSU0uUdBScCvKz1UIz8wzNooPLU4tckxOzi/NKwEA |
Select * From Win32_UserAccount |
|
C/Z0AQA |
SID |
|
88lPTsxxTE7OL80rAQA |
LocalAccount |
|
KykqTQUA |
true |
Privilege
It sets privilege as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded Privilege |
Decoded Privilege |
|
C04NSi0uyS9KDSjKLMvMSU1PBQA |
SeRestorePrivilege |
|
C04NScxO9S/PSy0qzsgsCCjKLMvMSU1PBQA |
SeTakeOwnershipPrivilege |
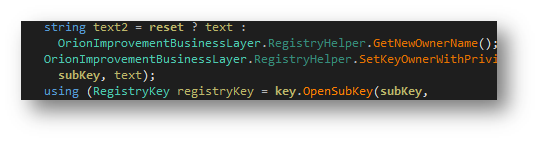
Set permission
It sets the current file to system permission as shown in figure below.
Information gathering of current processes
It gets information about current processes as shown in figure below.
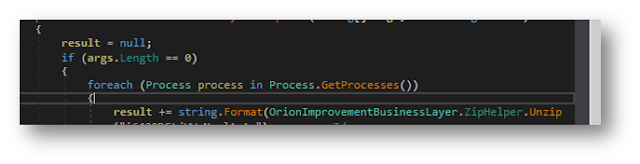 |
| Sunburst Solarwinds |
|
Encoded Value |
Decoded Value |
|
i6420DGtjVWoNqzlAgA |
[{0,5}] {1} |
|
C07NSU0uUdBScCvKz1UIz8wzNooPKMpPTi0uBgA |
Select * From Win32_Process |
|
c08t8S/PSy0CAA |
GetOwner |
|
i6420DGtjVWoNtTRNTSrVag2quWsNgYKKVSb1MZUm9ZyAQA |
[{0,5}] {1,-16} {2} {3,5} {4}\{5} |
|
CyjKT04tLvZ0AQA |
ProcessID |
|
80vMTQUA |
Name |
|
C0gsSs0rCSjKT04tLvZ0AQA |
ParentProcessID |
Gathering information of administrator of domain
It gathers information about the current administrator of the domain like hostname, account domain id, username, operating system version etc... As shown in figure below.
 |
| Sunburst Solarwinds |
Http Request
Before malware does http request, it resolves some important hashes with multiple checks as shown in figure below.
|
Encoded Value |
Decoded Value |
|
8873858923435176895UL |
expect |
|
6116246686670134098UL |
content-type |
|
2734787258623754862UL |
accept |
|
6116246686670134098UL |
content-type |
|
7574774749059321801UL |
user-agent |
|
8873858923435176895UL |
expect |
|
1475579823244607677UL |
100-continue |
|
11266044540366291518UL |
connection |
|
9007106680104765185UL |
referer |
|
11266044540366291518UL |
connection |
|
13852439084267373191UL |
keep-alive |
|
14226582801651130532UL |
close |
|
15514036435533858158UL |
if-modified-since |
|
16066522799090129502UL |
date |
|
qzaoVag2rFXwCAkJ0K82quUCAA |
{0} {1} HTTP/{2} |
Information stealer
It steals credentials of current users as shown in figure below.
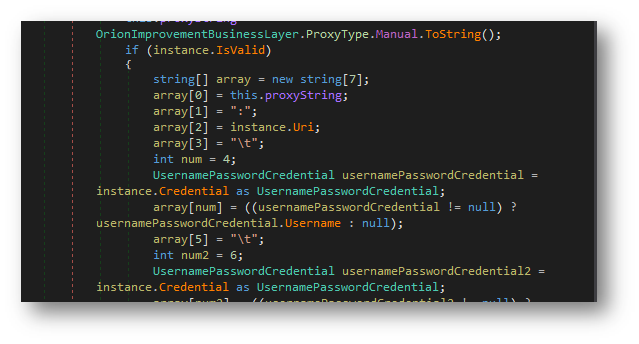 |
| Sunburst Solarwinds |
Parse service response
It uses http helper to define commands for executing engine function as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded
Value |
U4qpjjbQtUzUTdONrTY2q42pVapRgooABYxQuIZmtUoA |
|
Decoded
Value |
"\{[0-9a-f-]{36}\}"|"[0-9a-f]{32}"|"[0-9a-f]{16}" |
Http status code
It resolves important parameters when doing http request as shown in figure below.
 |
| Sunburst Solarwinds |
|
Encoded Value |
Decoded Value |
|
80zT9cvPS9X1TSxJzgAA |
If-None-Match |
|
UyotTi3yTFGyUqo2qFXSAQA |
"userId":"{0}", |
|
UypOLS7OzM/zTFGyUqo2qFXSAQA |
"sessionId":"{0}", |
|
UyouSS0oVrKKBgA |
"steps":[ |
|
UwrJzE0tLknMLVCyUorRd0ksSdWoNqjVjNFX0gEA |
"Timestamp":"\/Date({0})\/", |
|
U/LMS0mtULKqNqjVAQA= |
"Index":{0}, |
|
U3ItS80rCaksSFWyUvIvyszPU9IBAA |
"EventType":"Orion", |
|
U3ItS80r8UvMTVWyUgKzfRPzEtNTi5R0AA |
"EventName":"EventManager", |
|
U3IpLUosyczP8y1Wsqo2qNUBAA |
"DurationMs":{0}, |
|
UwouTU5OTU1JTVGyKikqTdUBAA |
"Succeeded":true, |
|
U/JNLS5OTE9VslKqNqhVAgA |
"Message":"{0}" |
|
SywoyMlMTizJzM/TzyrOzwMA |
application/json |
|
SywoyMlMTizJzM/Tz08uSS3RLS4pSk3MBQA |
application/octet-stream |
Base Uri implementation
It resolves important strings as shown in figure and table below.
 |
| Sunburst Solarwinds |
|
Encoded Value |
Decoded Value |
|
0y3Kzy8BAA |
-root |
|
001OLSoBAA |
-cert |
|
0y3NyyxLLSpOzIlPTgQA |
-universal_ca |
|
001OBAA |
-ca |
|
0y0oysxNLKqMT04EAA |
-primary_ca |
|
0y3JzE0tLknMLQAA |
-timestamp |
|
003PyU9KzAEA |
-global |
|
0y1OTS4tSk1OBAA |
-secureca |
|
K8jO1E8uytGvNqitNqytNqrVA/IA |
pki/crl/{0}{1}{2}.crl |
|
c8rPSQEA |
Bold |
|
c8rPSfEsSczJTAYA |
BoldItalic |
|
c60oKUp0ys9JAQA |
ExtraBold |
|
c60oKUp0ys9J8SxJzMlMBgA |
ExtraBoldItalic |
|
8yxJzMlMBgA |
Italic |
|
88lMzygBAA |
Light |
|
88lMzyjxLEnMyUwGAA |
LightItalic |
|
C0pNL81JLAIA |
Regular |
|
C07NzXTKz0kBAA |
SemiBold |
|
C07NzXTKz0nxLEnMyUwGAA |
SemiBoldItalic |
|
yy9IzStOzCsGAA |
opensans |
|
y8svyQcA |
noto |
|
SytKTU3LzysBAA |
freefont |
|
C84vLUpOdc5PSQ0oygcA |
SourceCodePro |
|
C84vLUpODU4tykwLKMoHAA |
SourceSerifPro |
|
C84vLUpO9UjMC07MKwYA |
SourceHanSans |
|
C84vLUpO9UjMC04tykwDAA |
SourceHanSerif |
|
S8vPKynWL89PS9OvNqjVrTYEYqNa3fLUpDSgTLVxrR5IzggA |
fonts/woff/{0}-{1}-{2}-webfont{3}.woff2 |
|
S8vPKynWL89PS9OvNqjVrTYEYqPaauNaPZCYEQA |
fonts/woff/{0}-{1}-{2}{3}.woff2 |
|
C87PSSwKz8xLKQYA |
SolarWinds |
|
03POLypJrQjIKU3PzAMA |
.CortexPlugin |
|
0/MvyszPAwA |
.Orion |
|
C88sSs1JLS4GAA |
Wireless |
|
C/UEAA |
UI |
|
C89MSU8tKQYA |
Widgets |
|
8wvwBQA |
NPM |
|
cyzIz8nJBwA |
Apollo |
|
c87JL03xzc/LLMkvysxLBwA |
CloudMonitoring |
|
88tPSS0GAA |
Nodes |
|
C8vPKc1NLQYA |
Volumes |
|
88wrSS1KS0xOLQYA |
Interfaces |
|
c87PLcjPS80rKQYA |
Components |
|
Ky7PLNAvLUjRBwA |
swip/upd/ |
|
06vIzQEA |
.xml |
|
Ky7PLNAPLcjJT0zRSyzOqAAA |
swip/Upload.ashx |
|
Ky7PLNB3LUvNKykGAA |
swip/Events |
User Agent
Malware resolves important parameters when it gets a user agent as shown in figure and table below.
 |
| Sunburst Solarwinds |
|
Encoded Value |
Decoded Value |
|
881MLsovzk8r0XUuqiwoyXcM8NQHAA |
Microsoft-CryptoAPI/ |
|
C87PSSwKz8xLKfYvyszP88wtKMovS81NzStxzskEkvoA |
SolarWindsOrionImprovementClient/ |
|
i/EvyszP88wtKMovS81NzSuJCc7PSSwKz8xLKdZDl9NLrUgFAA |
\OrionImprovement\SolarWinds.OrionImprovement.exe |
|
M9YzAEJjCyMA |
3.0.0.382 |
Key of base 64
Encoding key embedded in sample shown in figure and table below in table.
|
Encoded value |
Kyo0Ti9OzCkxKzXMrEyryi8wNTdKMbFMyquwSC7LzU4tz8gCAA |
|
Decoded Value |
rq3gsalt6u1iyfzop572d49bnx8cvmkewhj |
|
Encoded value |
M4jX1QMA |
|
Decoded Value |
0_-. |
Base64 Decode key
Decoding key embedded in sample shown in figure and table below in table.
 |
| Sunburst Solarwinds |
|
Encoded value |
K8gwSs1MyzfOMy0tSTfMskixNCksKkvKzTYoTswxN0sGAA |
|
Decoded Value |
ph2eifo3n5utg1j8d94qrvbmk0sal76c |
Decryption function for domain
Attacker uses the key below as shown in figure and table for decryption domain.
|
Encoded value |
MzA0MjYxNTO3sExMSk5JTUvPyMzKzsnNyy8oLCouKS0rr6is0o3XAwA |
|
Decoded Value |
0123456789abcdefghijklmnopqrstuvwxyz-_. |
Shutdown computer
Malware has the ability to shutdown current machine as shown in figure below.
|
Encoded value |
C04NzigtSckvzwsoyizLzElNTwUA |
|
Decoded Value |
SeShutdownPrivilege |
Yara Rule
/*
Yara Rule Set
Author: Mahmoud
Elmenshawy
Date:2019-05-1
Identifier:
SolarWinds Sunburst Backdoor
*/
rule
Sunburst_Backdoor {
meta:
Author = "Mahmoud Elmenshawy"
Description = " Sunburst Backdoor Rule
"
Sha256 =
"ce77d116a074dab7a22a0fd4f2c1ab475f16eec42e1ded3c0b0aa8211fe858d6"
strings:
$Encoded_Regx_Value =
"U4qpjjbQtUzUTdONrTY2q42pVapRgooABYxQuIZmtUoA" //
$Event_type =
"U3ItS80rCaksSFWyUvIvyszPU9IBAA"
$x3 = "C88sSs1JLS4GAA"
$x4 = "003PyU9KzAEA"
$x5 = "K8jO1E8uytGvNqitNqytNqrVA/IA"
$x6 = "SywrLstNzskvTdFLzs8FAA"
$x7 = "C84vLUpO9UjMC04tykwDAA"
$x8 = "cyzIz8nJBwA"
$x9 = "003PyU9KzAEA"
$x10 = "C84vLUpOdc5PSQ0oygcA
$x11 = "M9YzAEJjCyMA"
$x12 =
"07DP1NSIjkvUrYqtidPUKEktLoHzVTQB"
condition:
all of
them
}
References
- https://www.techradar.com/news/microsoft-has-discovered-yet-more-malware-affecting-solarwinds-orion.
- https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html.
If you wanna learn malware analysis you can check my YouTube channel I'm trying publish analysis of malware and some methods to analysis malwares.
Please don't forgot subscribe my channel Than you ♥
YouTube channel
https://www.youtube.com/channel/UCParXHaBXBmqRdHuVUg21pA
Contact Me : mahmoudmorsy372@gmail.com.










Comments
Post a Comment