Ragnarok Ransomware
Tactical report of Ransomware
Ragnarok
Identification
Vendor
|
Detection
|
ESET-NOD32
|
A Variant Of Win32/Filecoder.Ragnarok.A
|
TrendMicro
|
Ransom.Win32.RAGNAROK.A
|
ALYac
|
Trojan.Ransom.Ragnarok
|
The
following table contains list of artifacts that had been analyzed within this
document.
PE
Time stamp
|
MD
|
Size in bytes
|
Filename
|
Description
|
Monday 03 February 2020, 05.03.52
|
48452DD2506831D0B340E45B08799623
|
210.00 KB (215040 bytes)
|
since1969.exe
|
Main malicious
|
Summary
Ragnarok is
a piece of malicious software, classified as ransomware. Its discovery is
credited to Karsten
Hahn. It operates by
encrypting the data of infected devices, for the purpose of making ransom
demands for the decryption. As Ragnarok ransomware encrypts, all affected files
are appended with the ".ragnarok_cry" extension. To elaborate
on how files would appear following encryption, then a file titled something
like "1.jpg" would appear as "1.jpg.ragnarok_cry".
After this process is complete, a text file - "How_To_Decrypt_My_Files.txt"
is created on the desktop.
Technical
details
Ransomware
starts to resolve apis and libraries based on specific value as shown in figure
(1).
It resolves
libraries like kernel32.dll, Advapi32.dll, Mpr.dll
 |
| Figure (1) |
Mutex
Ransomware
Resolve api called CreateMutexA from library called kernel32.dll and creates
new mutex called name. To make sure that there is
only one version of ranowamre is running, if the mutex already exists so
ranomware will terminate as shown in figure (2).
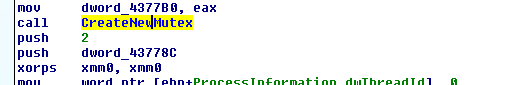 |
| Figure (2) |
It resolves
api called RegOpenKeyExA and RegQueryValueExA then try get current language of
machine by check registry path SYSTEM\CurrentControlSet\Control\Nls\Language
as shown in figure (3).
 |
| Figure (3) |
It checks if
operating system is 32 or 64 so in case of 32 bits it will create new process
as shown in figure (4) and in case of operating system is 64 it will create
process as shown in table and figure (5)
 |
| Figure (4) |
First
Case (32 bit)
Command
|
cmd_shadow
|
Process name
|
cmd.exe /c vssadmin delete shadows
/all /quiet
|
Purpose
|
To delete the Shadow Volume Copies
|
Second
case (64 bit)
It deletes
volume shadow copies and disables recovery of firewall as shown in figure (5) and
tables below.
 |
| Figure (5) |
Command
|
cmd_shadow
|
Process name
|
cmd.exe /c vssadmin delete shadows
/all /quiet
|
Purpose
|
To delete the Shadow Volume Copies
|
lpCommandLine
|
cmd.exe /c bcdedit /set {current}
recoveryenabled no
|
lpCommandLine
|
cmd.exe /c bcdedit /set {current}
recoveryenabled no
|
lpApplicationName
|
cmd_firewall
|
It generates
new AES key as shown in figure (6)
 |
| Figure (6) |
Aes_key_rand
- ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789.
It gets computer
name as shown in figure (7).
 |
| Figure (7) |
Malware
trying to get public and private ip address of machine as shown in figure (8).
 |
| Figure (8) |
It resolves
apies to search for files and detect all drives in pc as
shown in figure (9).
 |
| Figure (9) |
I collected
most of configurations of ransomware as shown in two figures (10) and (11)
below.
 |
| Figure (10) |
 |
| Figure (11) |
It adds
extension ragnaroks at every file that
encrypted.
After
encryption finished it displays readme message at the end as shown in figure (12).
 |
| Figure (12) |
Yara Rule
/*
Yara Rule Set
Author: Mahmoud
Elmenshawy
Date:2019-11-17
Identifier: BitPaymer Ransomware
*/
private rule IsPE
{condition:
// MZ signature at offset 0 and ...
uint16(0) == 0x5A4D and
// ... PE signature at offset stored in MZ header at 0x3C
uint32(uint32(0x3C)) == 0x00004550}
rule RagrokRansomware{
meta:
Author
= "Mahmoud Elmenshawy"
Description = " Ragrok Ransomware Rule for detecting Main
file"
MD5 = "48452DD2506831D0B340E45B08799623"
strings:
$x1
="!!ReadMe_To_Decrypt_My_Files.txt".
$x2 ="cmd.exe /c bcdedit /set {current} recoveryenabled no".
$x3 =" cmd.exe /c bcdedit /set {current} bootstatuspolicy ignoreallfailures".
condition:
All of them and IsPE
If you wanna learn malware analysis you can check my YouTube channel I'm trying publish analysis of malware and some methods to analysis malwares.
Please don't forgot subscribe my channel Than you ♥
YouTube channel
https://www.youtube.com/channel/UCParXHaBXBmqRdHuVUg21pA
Malware
analyst :
Mahmoud El Menshawy.
Contact Me : mahmoudmorsy372@gmail.com.
linkedin profile : https://www.linkedin.com/in/mahmoudmorsy1/.
Contact Me : mahmoudmorsy372@gmail.com.
linkedin profile : https://www.linkedin.com/in/mahmoudmorsy1/.


Comments
Post a Comment