Everis-Ransomware-Attack
Tactical report of ransomware Bitpaymer
_
Identification
Vendor
|
Detection
|
Kaspersky
|
Trojan.Win32.DelShad.bnq
|
Malwarebytes
|
Ransom.Bitpaymer
|
TrendMicro
|
Ransom.Win32.FRIEDEX.E
|
Prevalence:-
Ransomware Attacks Hit Everis and
Spain's Largest Radio Network, Everis, an NTT DATA company and one of Spain's largest
managed service providers (MSP), had its computer systems encrypted today in a
ransomware attack, just as it happened to Spain's largest radio station Cadena
SER (Sociedad Española
de Radiodifusión).
While the ransomware attacks were not
yet publicly acknowledged by the company, the ransom note left on Everis'
encrypted computers has already leaked and Bleeping Computer can confirm that
the MSP's data was infected using the BitPaymer ransomware.
1.Indicators of compromise
The threat phases are:
1. An everis user access to a
compromised website where the source code was modified to show a fake browser
update and download a file.
2. The file is a JavaScript code (JS)
which infects the device with a C2C malware categorized as “EMOTET”. This
JavaScript creates additional exe files.
3. Once the attackers controls the
infected device, install a PowerShell post explotation framework called
Empire1. With Empire Framework in the infected device, the attacker enumerates
the network and get credentials form the infected device cache. With this,
different Empire installations is seen in different hosts and servers.
4. Attackers distribute a ransomware
family called “BitPaymer/IEncrypt” to everis devices through compromised hosts
and servers.
1.1.1 Compromised website
A compromised website with a
modification of the source code to simulate a fake browser update.
URL: hxxps://esancendoc[.]esan[.]edu[.]pe/
- Compromised website.
1.1.2 Malicious file
Compromised website downloads a JS file “Chrome.Update.3f61f4.js”. JS
script is a Dropper which downloads “crhome.update.3f61f4.exe” categorized as
EMOTET. An additional exe “d0409052256c6efc85b155f58cc03f70.exe” file is
created and executed.
Indicators of Compromise
Chrome.Update.3f61f4.js
MD5: a9db3444e9c50da5ce6845ccc116255c.
MD5: c1a5725f45e6a35bd82852210e29f941.
URL to download the malware
hxxps://click[.]clickanalytics208[.]com/s_code[.]js?cid=240&v=73a55f6de3dee2a751c3
EMOTET -
crhome.update.3f61f4.exe
SHA256:
628c181e6b9797d8356e43066ae182a45e6c37dbee28d9093df8f0825c342d4c
IP:
195[.]123[.]213[.]19
Port: 443
EMOTET -
d0409052256c6efc85b155f58cc03f70.exe
SHA256: 1d778359ab155cb190b9f2a7086c3bcb4082aa195ff8f754dae2d665fd20aa05.
1.1.3 Lateral
movement
Lateral
movement is performed by the attacker through the PowerShell post-explotation
framework called Empire. Lateral movement was performed through sysinternals
tool “psexesvc.exe”.
Indicators
of Compromise.
Empire
Framework
IP: 185[.]92[.]74[.]215.
Port: 443.
1.1.4 Infection
Malware is
distributed from compromised assets to affected endpoints.
Indicators
of Compromise.
BitPaymer/IEncrypt
SHA256: bd327754f879ff15b48fc86c741c4f546b9bbae5c1a5ac4c095df05df696ec4f
- evrs.exe.
The
following table contains a list of artifacts that had been analyzed within this
document.
PE
timestamp
|
MD5
|
Size in
bytes
|
File name
|
Description
|
1994-05-18
19:56:20
|
e19d2c46521767f3b836e9861eecea9c
|
148 KB
(151,552 bytes)
|
N/A
|
Dropper
|
This
ransomware packed with new custom packing as shown in figure (1).
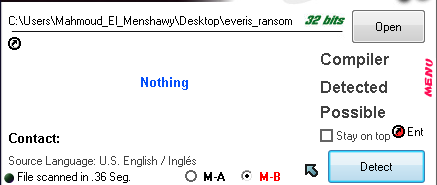 |
| Figure (1) |
Let’s see how
to unpack it.
Unpacking
- Set breakpoint at virtualalloc api then run as shown in figure (2).
 |
| Figure (2) |
- Continue stepping till see loop that resolves section .txt and other sections as shown in figure (3).
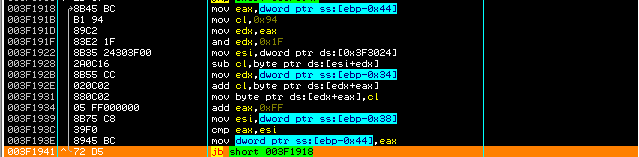 |
| Figure (3) |
- Continue stepping till find function as shown in figure (4) then go inside it.
 |
| Figure (4) |
- Continue stepping till find jmp near eax as shown in figure (5).
 |
| Figure (5) |
After
jumping, we reach to correct malicious code then dumps code as shown in figure
(6).
 |
| Figure (6) |
PE
timestamp
|
MD5
|
Size in
bytes
|
File name
|
Description
|
2019/03/12
Tue 07:20:45 UTC
|
F46C341753E7DC50C345B0B21D9CC93F
|
156 KB
(159,744 bytes)
|
N/A
|
Encryption
+ Payload
|
Simple trick to stop ransomware
Kill Switch File
Bitpaymer
try to open file called C:\\aaa_TouchMeNot_.txt as
shown in figure (7) with the following parameters as shown in table.
 |
| Figure (7) |
FileName
|
C:\\aaa_TouchMeNot_.txt
|
dwDesiredAccess
|
GENERIC_READ
|
dwShareMode
|
FILE_SHARE_READ|FILE_SHARE_WRITE
|
dwCreationDisposition
|
OPEN_EXISTING
|
Case (1)
So if the
file exists, it will terminate without any encryption to files.
Case (2)
If the file
is not exist, it will encrypt files.
So for
simplification if you create file in c directory with same name and contains
any data, then ransomware will not infect you.
Obfuscation
Ransomare is
fully obfuscation, it creates strings during runtime, it resolves apis based on
2 value pushed to specific algorithm and
executes in random address in memory.
Technical
analysis
It handles
to current filename of ransomware , it gets operating system version as shown
in figure (8).
 |
| Figure (8) |
It
determines if operating system is 64 or 32 bit as shown in figure (9) with the following
parameters as shown in table.
 |
| Figure (9) |
hProcess
|
0013FC18
|
InfoClass
|
1A
|
Buffer
|
0013FC08
|
Bufsize
|
0x4
|
It
enumerates path of software as shown in figure (10) with the following
parameters as shown in table below.
 |
| Figure (10) |
Access
|
KEY_ENUMERATE_SUB_KEYS|13FB80
|
Subkey
|
Null
|
hKey
|
0x586300
|
It repeats
operation of enumeration to resolve full path of registry key and close handle registry
as shown in figure (11).
 |
| Figure (11) |
Full
path
- "SOFTWARE/Microsoft/Windows/CurrentVersion/Policies/System".
It
enumerates registry key as shown in figure (12) with the following parameters
as shown in table to resolve important strings.
 |
| Figure (12) |
hKey
|
0x0
|
Value
|
0013FA90
|
Index
|
13FA94
|
Resolved
values
- "EnableVirtualization”
- "EnableInstallerDetection"
- “PromptOnSecureDesktop"
- "EnableLUA"
- "EnableSecureUIAPaths"
- "ConsentPromptBehaviorAdmin"
- "ValidateAdminCodeSignatures"
- "EnableCursorSuppression"
- "EnableUIADesktopToggle"
- "ConsentPromptBehaviorUser"
- “dontdisplaylastusername"
- "legalnoticecaption"
- "legalnoticetext"
- "scforceoption"
- "shutdownwithoutlogon"
- "undockwithoutlogon"
- "FilterAdministratorToken"
- "ConsentPromptBehaviorUser".
It resolves
api called RegQueryValue and gets the data and type of value EnableLUA as shown
in figure (13) with the following api parameters as shown in table.
 |
| Figure (13) |
hKey
|
0x586D50
|
ValueName
|
NULL
|
Reserved
|
0013FBA0
|
It retrieves
information about the current system as shown in figure (14).
 |
| Figure (14) |
It resolves
api called CreateEvent and create new event as shown in figure (15) with the
following parameters as shown in table.
 |
| Figure (15) |
EventName
|
"P2. @"
|
InitiallySignaled
|
TRUE
|
ManualReset
|
FALSE
|
pSecurity
|
00000001
|
Expands
environment-variable strings
[“%ProgramData%”,”%windir%”,”%temp%”,”%AppData%”] and replaces them with the values defined for the current user as shown in figure (17).
[“%ProgramData%”,”%windir%”,”%temp%”,”%AppData%”] and replaces them with the values defined for the current user as shown in figure (17).
 |
| Figure (17) |
The reason
of that is preventing ransomware from encrypting files in these folders.
It resolves
ransomware message as shown in figure (18), once encryption finished it will
create it at each folders.
 |
| Figure (18) |
It decodes
string called .3v3r1s as shown in figure (19),
this string will be an extension of readme file at
each directory that ransomare will encrypt its files.
 |
| Figure (19) |
It resolves
key used for encryption data as shown in figure (20).
Key
- "MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAslY99/86gD/dS9kosI+Am20UDt//ms4TQmVQtmiwLf5oFArtmbbPEikgu0JHMmMhHIe7F8GoSLYQWUBiqs679xN5T6i0Mjp5N4Dc5WSVAtzxOCjDfXdORgzL/sGc8Yp4QS9OMmyrXyUYjmrvO05vjxU7r+m2BdKizo6F4TmzkgYNRPMZXJI+rJjJrRP".
It resolves
api called ExitProcess so once the encryption
ends it will exit process immediately as shown in figure (21).
It attempt
to start specific service if it couldn’t start it then it will repeat steps and
creates new process as shown in figure (22).
It retrieves
the short path form of the path of ransomware as shown in figure (23).
So the short
path will be:
- "C:\Users\MAHMOU~1\Desktop\EVERIS~1".
It generates
new random key using windows api cryptographic as shown in figure (24).
 |
| Figure (24) |
It resolves
another random string with 9 mixed characters and
numbers as shown in figure (25).
 |
| Figure (25) |
The file “N88O21Cry” created in path called C:\Users\UserName\AppData\Roaming.
And assign
time and date to it.
 |
| Figure (26) |
It Gets
short of file “N88O21Cry” as shown in figure
(27).
| Figure (27) |
Short path:
- "C:\Users\MAHMOU~1\AppData\Roaming\N88O21~1"
It resolves
api called CreateProcessW as shown in figure (27) and create new process with
the following parameters as shown in table.
| Figure (27) |
ModuleFileName
|
"C:\Users\MAHMOU~1\AppData\Roaming\N88O21~1:bin
C:\Users\MAHMOU~1\Desktop\EVERIS~1"
|
CommandLine
|
Null
|
pProcessSecurity
|
NuLL
|
pThreadSecurity
|
00000001
|
InheritHandles
|
TRUE
|
The reason
of this process is deleting shadow copy and start encrypting files as shown in
figure (28), (29), (30).
| Figure (28) |
 |
| Figure (29) |
 |
| Figure (30) |
At the end
it adds extension called .3v3r1s to each
encrypted file and adds readme file to each
files that had been encrypted as shown in figure (31).
 |
| Figure (31) |
Ransom
note
 |
| Figure (32) |
Email
address
- Hxxp\\SYDNEY[.]WILEY@PROTONMAIL[.]COM.
- HXXP\\EVANGELINA[.]MATHEWS@TUTANOTA[.]COM.
Yara
Rule
/*
Yara Rule Set
Author: Mahmoud
Elmenshawy
Date:2019-11-17
Identifier: BitPaymer Ransomware
*/
private rule IsPE
{condition:
// MZ signature
at offset 0 and ...
uint16(0) ==
0x5A4D and
// ... PE
signature at offset stored in MZ header at 0x3C
uint32(uint32(0x3C)) == 0x00004550}
rule NotPetya{
meta:
Author = "Mahmoud
Elmenshawy"
Description = " BitPaymer Rule for detecting Installer "
MD5 =
"e19d2c46521767f3b836e9861eecea9c"
strings:
$x1
=".C:\\aaa_TouchMeNot_.txt".
$x2 ="30 34 51 75 55 52 58 2E 70 64
62".
$x3
="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+".
condition:
All
of them and IsPE
Referances:
- https://www.mcafee.com/blogs/other-blogs/other-blogs/mcafee-labs/spanish-mssp-targeted-by-bitpaymer-ransomware/.
- https://www.cbronline.com/news/everis-hacked-ransomware.
- https://howtoremove.guide/everis-ransomware-attack/.
If you wanna learn malware analysis you can check my YouTube channel I'm trying publish analysis of malware and some methods to analysis malwares.
Please don't forgot subscribe my channel Than you ♥
YouTube channel
https://www.youtube.com/channel/UCParXHaBXBmqRdHuVUg21pA
Malware analyst : Mahmoud El Menshawy.
Contact Me : mahmoudmorsy372@gmail.com.
linkedin profile : https://www.linkedin.com/in/mahmoudmorsy1/.






Comments
Post a Comment