ransomware REvil Sodinokibi
Tactical report of ransomware SODINOKIBI
Identification
Vendor
|
Detection
|
ESET-NOD32
|
Win32/Filecoder.Sodinokibi.B
|
Fortinet
|
W32/Sodinokibi.B!tr.ransom
|
McAfee
|
Ransom-Sodinokibi.b
|
TrendMicro
|
Ransom.Win32.SODINOKIBI.AUWSY
|
Summary
Sodinokibi
ransomware is known as REvil that’s created by cybercriminals. They
use it to encrypt files included in system and prevent them from accessing till
you pay amount of money to the author of ransomware. It puts ransom messages at
every folder that ransomware encrypts it.it changes desktop wallpaper.the
ransomware messages describe instructions about how to decrypted and recover
your files again.
Technical analysis
The
following table contains a list of artifacts that had been analyzed within this
document.
PE timestamp
|
MD5
|
Size in bytes
|
File name
|
Description
|
2018-10-06 Sat 05:26:33 UTC
|
e713658b666ff04c9863ebecb458f174
|
536 KB (548,864 bytes)
|
I
tuoi documenti del caso.doc.exe
|
Spread and encryption
|
Packing
The ransomware is packed with custom packer. Let’s see
how we can unpack it.
When we run ransomware then it needs permission to create
another process with the same name of ransomware.
So use pe-seive with specific pid to dumped what actually
running at this time as shown in figure (1).
 |
| Figure (1) |
As we shown in figure (2) this is ransomware after
unpacking but there is no imports that’s mean it builds import address table
within specific function.
 |
| Figure (2) |
So if we go through code we find correct part that
initializes import address table as shown in figure (3) so what we do is let
program run this subroutine then it will resolves apis and after that dump the
code with correct apis as shown in figure (4).
 |
| Figure (3) |
 |
| Figure (4) |
Malware behavior
It decodes string called Global\UUID with custom algorithm
as shown in figure (5).
 |
| Figure (5) |
It creates mutex called Global\GUID of pc with the
following parameters as shown in figure (6) to ensure that there is only
version of malware running.
 |
| Figure (6) |
If it couldn’t create mutex then the ransomare exit as
shown in figure (7).
 |
| Figure (7) |
It decodes configuration with CRC32
algorithm as shown in figure (7),(8).
 |
| Figure (7) |
 |
| Figure (8) |
Decoded content
Name
|
value
|
Description
|
pk
|
1g3/QEQPOQ7S3fBLZ0wvu/B9NfpLLvf8mByoN3or9E0=
|
Encryption
key ( in my case)
|
pid
|
5
|
Personal
id
|
sub
|
367
|
Another
id
|
dbg
|
false
|
Debug
mode
|
fast
|
true
|
Fast
mode
|
Wipe
|
true
|
Enable
wipe of specific path
|
wht
|
Whitelist
directory
|
fld
|
The ransomawre skips encrypt these listed folders.
- program files(x86).
- windows.
- boot.
- perflogs.
- appdata.
- mozilla.
- program.
It gets system time, native system info and disables Wow64FsRedirection
as shown in figure (9), (10).
 |
| Figure (9) |
 |
| Figure (10) |
It allocates space in memory using the following
parameters as shown in figure (11) and table.
 |
| Figure (11) |
Name
|
Value
or purpose
|
flProtect
|
PAGE_EXECUTE_READWRITE
|
flAllocationType
|
MEM_COMMIT
or MEM_RESERVE
|
dwSize
|
(13824) bytes
|
lpAddress
|
NULL
|
It gets path of ransomware if it exit it will enumeration
current running window otherwise it will exit as shown in figure (13).
 |
| Figure (13) |
It decodes string explorer.exe, check for Sid, list
current processes and start handling to process explorer.exe as shown in figure
(14).
 |
| Figure (14) |
It impersonates the security context of a logged-on user
as shown in figure (15).
 |
| Figure (15) |
It continues decoding configuration using CRC32 algorithm as
shown in figure (17).
 |
| Figure (17) |
Decoded content
Name
|
Description
|
prc
|
Process
to kill
|
dmn
|
Domain
to contact
|
net
|
Network
resources
|
nbody
|
Ransomware
notes
|
exp
|
Dun
know
|
Img
|
Message
of desktop
|
It creates the following keys especially in this path SOFTWARE\recfg
with the following parameters as shown in figure (18).
Keys
- pk_key.
- sub_key.
- sk_key.
- 0_key.
- rnd_ext.
 |
| Figure (18) |
It resolves random huge
string as shown in figure (19) maybe this string used for encryption files.
String
- (i8ERPE9y10uhHMAiDfEr9lM39XpH3uWWIhloaDzemMgeEVTNLYNXTwEIMziiXVXOZaCqtbz9fgVr3/hH2mUKEORksyshZ80O3vg1).
 |
| Figure (19) |
It gets volume processor
type and volume serial number and encrypt them using CRC32 as
shown in figure (20).
 |
| Figure (20) |
It gets data from computer like :-
- Current username.
- Computer name.
- Current Language.
- It determines if the machine is work-group or server.
- Operating system version.
- Keyboard Layout.
- Available space in each disk.
 |
| Figure (21) |
It creates new key with the
following parameters as shown in figure(22).
lpValueName => stat.
lpSubKey => SOFTWARE\recfg.
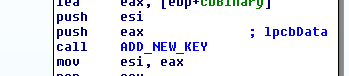 |
| Figure (22) |
It executes shell with this
command to delete recovery and prevent you restore your files again as shown in
figure (23).
 |
| Figure (23) |
Command
- cmd /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set {{default}} recoveryenabled No & bcdedit /set {{default}} bootstatuspolicy ignoreallfailures.
It gets files in c drive also
enumerates net resources and preparing them for encryption as shown in figure
(24).
 |
| Figure (24) |
Command and control
server
- It gernerates random url.
- It uses post request with created URLs.
User agent
 |
| User Agent |
 |
| send request |
 |
| Content type |
 |
| Receive |
 |
| Recieve |
So what we receive?
It changes configurations in
browser.
- Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0\.
- Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1\.
- Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2\.
- Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3\.
- Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\4\.
It decodes important strings
maybe these strings used for connections as shown in figure (25).
 |
| Figure (25) |
Strings
- wp-content.
- Static.
- Content.
- Include.
- Uploads.
- News.
- Data.
- Admin.
- ("Wp-content").
- Images.
- Pictures.
- Temp.
- Tmp.
- Graphic.
- Assests.
- Pics.
- Game.
- Jpg.
- Png.
- Gif.
Important Urls found
in sample.
- craftingalegacy.com.
- g2mediainc.com.
- brinkdoepke.eu.
- vipcarrental.ae.
- autoteamlast.de.
- hostastay.com;gave.
Readme file
If you wanna learn malware analysis you can check my YouTube channel I'm trying publish analysis of malware and some methods to analysis malwares.
Please don't forgot subscribe my channel Than you ♥
YouTube channel
https://www.youtube.com/channel/UCParXHaBXBmqRdHuVUg21pA
Malware analyst : Mahmoud El Menshawy.
Contact Me : mahmoudmorsy372@gmail.com.
Contact Me : mahmoudmorsy372@gmail.com.





Thanks for sharing your blog. It was really good. If you are looking for Sodinokibi ransomware services for protecting your data, then Fast Data Recovery is your one stop solution. Feel free to contact us or visit our website .
ReplyDeleteThank you sir!
ReplyDeletewe can communicate if you wanna any help . what's your personal email? LinkedIn etc..